Cold vs Hot Wallets - Which Crypto Storage is Better?
Choosing between cold and hot wallets is one of the most important decisions in cryptocurrency security. This comprehensive guide explains the fundamental differences, security implications, and practical use cases to help you make the right choice for your crypto storage needs in 2025.
Understanding Wallet Types in 2025
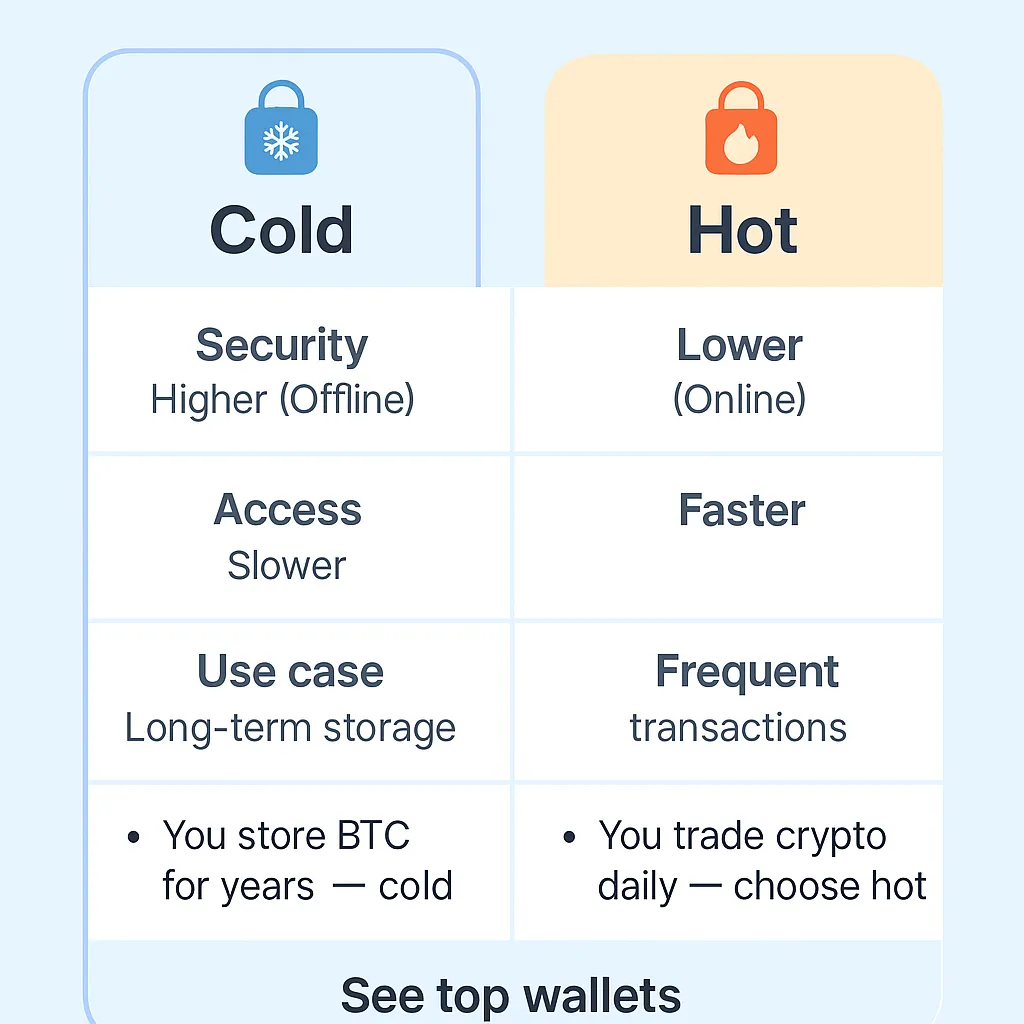
The cryptocurrency wallet landscape has evolved significantly, but the fundamental distinction between cold (offline) and hot (online) storage remains crucial for security. With over $3 billion lost to crypto hacks in 2024, understanding proper storage methods is more important than ever.
Cold wallets, also known as hardware wallets or offline storage, keep your private keys completely disconnected from the internet. Hot wallets, including mobile apps and browser extensions, maintain internet connectivity for convenient access to decentralized applications and trading platforms.
The choice between cold and hot storage isn't binary – most experienced users employ a hybrid approach, using both types strategically based on their specific needs and risk tolerance.
Cold Wallets: Maximum Security Storage
What Are Cold Wallets?
Cold wallets are cryptocurrency storage devices that keep your private keys completely offline, isolated from internet-connected devices. They generate and store private keys in a secure environment that never touches the internet, making them virtually immune to online attacks.
Types of Cold Storage
Hardware Wallets
Physical devices specifically designed for cryptocurrency storage:
- Ledger Nano S Plus: Entry-level hardware wallet supporting 5,500+ cryptocurrencies
- Ledger Nano X: Premium model with Bluetooth connectivity and mobile app support
- Trezor Model One: Open-source hardware wallet with strong security features
- Trezor Model T: Advanced model with touchscreen and expanded cryptocurrency support
- Tangem Wallet: Card-based hardware wallet with NFC technology
Paper Wallets
Physical documents containing private keys and addresses:
- Generated offline using secure random number generators
- Printed on paper or engraved on metal for durability
- Completely immune to digital attacks
- Requires careful physical security and backup procedures
Cold Wallet Advantages
Maximum Security
Cold wallets provide the highest level of security available for cryptocurrency storage. Private keys never touch internet-connected devices, making them immune to:
- Malware and viruses
- Phishing attacks
- Remote hacking attempts
- Exchange hacks and platform failures
- SIM swapping and social engineering
Long-Term Storage
Ideal for "hodling" strategies where cryptocurrencies are held for extended periods without frequent transactions. Cold storage encourages disciplined investing by making impulsive trades more difficult.
Multi-Signature Support
Many hardware wallets support multi-signature setups, requiring multiple devices or parties to authorise transactions, further enhancing security for large holdings.
Recovery Options
Hardware wallets use standardised recovery phrases (BIP39) that can restore access to funds even if the device is lost or damaged.
Cold Wallet Disadvantages
Inconvenience
Every transaction requires physical access to the device and manual confirmation, making frequent trading or DeFi interactions cumbersome.
Initial Cost
Hardware wallets require upfront investment ($50-200), though this cost is minimal compared to the security benefits for significant holdings.
Physical Risks
Devices can be lost, stolen, or damaged. While funds remain recoverable through seed phrases, physical security becomes crucial.
Technical Complexity
Setting up and using cold wallets requires more technical knowledge than hot wallets, potentially intimidating new users.
Hot Wallets: Convenience and Accessibility
What Are Hot Wallets?
Hot wallets are cryptocurrency storage applications that maintain internet connectivity, allowing instant access to funds and seamless interaction with blockchain networks and decentralized applications.
Types of Hot Wallets
Mobile Wallets
Smartphone applications for on-the-go cryptocurrency management:
- Trust Wallet: Multi-chain mobile wallet with dApp browser
- MetaMask Mobile: Ethereum-focused with extensive DeFi integration
- Coinbase Wallet: User-friendly with educational resources
- Phantom: Solana ecosystem specialist
- Keplr Mobile: Cosmos ecosystem integration
Browser Extension Wallets
Desktop browser plugins for web-based cryptocurrency interactions:
- MetaMask: Industry standard for Ethereum and EVM chains
- Phantom: Leading Solana wallet with clean interface
- Keplr: Cosmos ecosystem gateway
- Rabby: Multi-chain wallet with advanced features
Desktop Wallets
Full-featured applications installed on computers:
- Exodus: Multi-currency wallet with built-in exchange
- Atomic Wallet: Decentralized wallet with staking features
- Electrum: Bitcoin-focused with advanced features
Hot Wallet Advantages
Instant Access
Hot wallets provide immediate access to funds for trading, DeFi interactions, and daily transactions without physical device requirements.
DeFi Integration
Seamless connection to decentralised exchanges, lending protocols, and yield farming opportunities through built-in dApp browsers.
User-Friendly
Intuitive interfaces make cryptocurrency accessible to beginners, with features like QR code scanning and address book management.
Multi-Chain Support
Modern hot wallets support multiple blockchain networks, allowing users to manage diverse cryptocurrency portfolios from a single application.
Regular Updates
Automatic updates ensure compatibility with new protocols and security patches without user intervention.
Hot Wallet Disadvantages
Security Vulnerabilities
Internet connectivity exposes hot wallets to various attack vectors:
- Malware and keyloggers
- Phishing websites and fake applications
- Browser vulnerabilities and extensions
- Mobile device compromises
- Man-in-the-middle attacks
Platform Dependency
Reliance on third-party platforms creates risks from poor security practices, data breaches, or service discontinuation.
Temptation to Overtrade
Easy access can lead to impulsive trading decisions and increased exposure to market volatility.
Comprehensive Feature Comparison
Security Comparison
| Security Aspect | Cold Wallets | Hot Wallets |
|---|---|---|
| Private Key Storage | Offline, hardware-protected | Online, software-protected |
| Internet Exposure | Never connected | Always connected |
| Malware Resistance | Immune | Vulnerable |
| Phishing Protection | High (device verification) | Low (user dependent) |
| Physical Security | Required | Device dependent |
| Recovery Options | Seed phrase backup | Varies by wallet |
Usability Comparison
| Usability Factor | Cold Wallets | Hot Wallets |
|---|---|---|
| Transaction Speed | Slow (manual confirmation) | Fast (instant) |
| DeFi Access | Limited (requires connection) | Native integration |
| Mobile Access | Limited | Full featured |
| Setup Complexity | Moderate to high | Low to moderate |
| Cost | $50-200 initial | Free |
| Portability | Physical device required | Available anywhere |
Security Best Practices
Cold Wallet Security
- Purchase from Official Sources: Only buy hardware wallets directly from manufacturers
- Verify Authenticity: Check for tamper-evident seals and authenticity certificates
- Secure Seed Phrase Storage: Write down recovery phrases on paper, store in multiple secure locations
- Regular Firmware Updates: Keep device firmware updated for latest security patches
- Test Recovery Process: Verify seed phrase recovery works before storing large amounts
- Physical Security: Store devices in secure locations, consider safety deposit boxes
Hot Wallet Security
- Use Reputable Wallets: Choose well-established wallets with strong security track records
- Enable All Security Features: Use biometric locks, PINs, and two-factor authentication
- Regular Updates: Keep wallet applications and operating systems updated
- Verify URLs: Always double-check website URLs and app store listings
- Limit Stored Amounts: Keep only small amounts needed for regular transactions
- Backup Seed Phrases: Securely store recovery phrases offline
Practical Use Case Scenarios
Long-Term Investment (Cold Wallet Recommended)
Scenario: You've accumulated 2 BTC and 50 ETH over several years and plan to hold for the next decade.
Solution: Store 90% in a Ledger Nano X with seed phrase backed up in multiple secure locations. Keep 10% in a hot wallet for potential opportunities.
Active DeFi Participation (Hot Wallet Required)
Scenario: You actively provide liquidity to Uniswap pools and participate in yield farming across multiple protocols.
Solution: Use MetaMask for primary DeFi interactions, connected to a hardware wallet for transaction signing when possible.
Daily Cryptocurrency Usage (Hot Wallet Preferred)
Scenario: You regularly pay for goods and services with cryptocurrency and trade frequently.
Solution: Mobile wallet like Trust Wallet for daily transactions, with larger holdings secured in cold storage.
Institutional Holdings (Cold Wallet Essential)
Scenario: Managing cryptocurrency treasury for a company or investment fund.
Solution: Multi-signature cold storage setup with hardware wallets distributed among key stakeholders.
Hybrid Storage Strategies
The 80-20 Rule
Store 80% of holdings in cold storage for security, keep 20% in hot wallets for accessibility and opportunities. This balance provides security while maintaining flexibility.
Tiered Security Approach
- Tier 1 (Cold Storage): Long-term holdings, emergency funds
- Tier 2 (Hardware + Hot): Medium-term investments, DeFi positions
- Tier 3 (Hot Wallet): Daily spending, trading funds
Activity-Based Allocation
- HODLing: 95% cold, 5% hot
- Moderate Trading: 70% cold, 30% hot
- Active DeFi: 50% cold, 50% hot
- Day Trading: 20% cold, 80% hot
How to Choose the Right Wallet
Assessment Questions
- How much cryptocurrency do you own?
- Under $1,000: Hot wallet acceptable
- $1,000-$10,000: Consider cold storage
- Over $10,000: Cold storage essential
- How often do you transact?
- Rarely: Cold wallet preferred
- Weekly: Hybrid approach
- Daily: Hot wallet primary
- What's your technical expertise?
- Beginner: Start with a reputable hot wallet
- Intermediate: Hybrid approach
- Advanced: Custom security setup
- Do you use DeFi protocols?
- Never: Cold storage sufficient
- Occasionally: Hardware wallet + hot wallet
- Frequently: Hot wallet with hardware signing
Final Recommendations
For Beginners
Start Simple: Begin with a reputable hot wallet like Coinbase Wallet or Trust Wallet. Learn the basics of cryptocurrency management before investing in hardware wallets.
For Intermediate Users
Hybrid Approach: Use a hardware wallet (Ledger Nano X or Trezor Model T) for long-term storage, maintain a hot wallet for regular transactions and DeFi activities.
For Advanced Users
Multi-Layered Security: Implement tiered storage with multiple hardware wallets, multi-signature setups, and specialised hot wallets for different activities.
For Institutions
Enterprise Solutions: Use institutional custody services combined with multi-signature cold storage and comprehensive security policies.
Universal Principles
- Never store more than you can afford to lose in hot wallets
- Always backup seed phrases securely
- Regularly review and update security practices
- Stay informed about new threats and solutions
- Test recovery procedures before storing large amounts
When to Use Each Wallet Type
Use Cold Wallets When:
- Storing significant amounts of cryptocurrency (>$10,000)
- Planning long-term investment strategies
- Prioritizing maximum security over convenience
- Managing institutional or business cryptocurrency holdings
- Creating inheritance or estate planning arrangements
- Operating in high-risk environments or jurisdictions
Use Hot Wallets When:
- Making frequent transactions or trades
- Participating in DeFi protocols and yield farming
- Using cryptocurrency for daily payments
- Learning cryptocurrency basics with small amounts
- Needing immediate access to funds
- Interacting with new protocols or applications
Use Both When:
- Building a comprehensive cryptocurrency strategy
- Balancing security with accessibility needs
- Managing diverse cryptocurrency activities
- Optimising for both long-term growth and short-term opportunities
- Implementing proper risk management practices
Cost Analysis: Cold vs Hot Wallets
Initial Setup Costs
| Wallet Type | Hardware Cost | Setup Time | Learning Curve | Ongoing Costs |
|---|---|---|---|---|
| Cold Wallets | $50-200 | 1-2 hours | Moderate-High | Firmware updates (free) |
| Hot Wallets | Free | 15-30 minutes | Low-Moderate | Transaction fees only |
Long-Term Value Proposition
While cold wallets require upfront investment, they provide significant long-term value:
- Security ROI: Prevents potential losses from hacks or theft
- Peace of Mind: Reduces stress and anxiety about fund security
- Insurance Value: Some insurance policies require hardware wallet usage
- Resale Value: Hardware wallets retain value and can be resold
- Multi-Asset Support: One device supports thousands of cryptocurrencies
Enterprise and Institutional Considerations
Corporate Wallet Strategies
Businesses and institutions have unique requirements for cryptocurrency storage:
Multi-Signature Cold Storage
- Governance Structure: Require multiple executives to authorize transactions
- Geographic Distribution: Store signing devices in different locations
- Succession Planning: Ensure business continuity if key personnel leave
- Audit Compliance: Maintain detailed records for regulatory compliance
Operational Hot Wallets
- Daily Operations: Small amounts for regular business transactions
- API Integration: Automated payments and treasury management
- Employee Access: Controlled access for authorized personnel
- Real-Time Monitoring: 24/7 monitoring and alert systems
Regulatory Compliance
Different jurisdictions have varying requirements for cryptocurrency custody:
- United States: CFTC and SEC guidance on custody requirements
- European Union: MiCA regulations for crypto asset service providers
- United Kingdom: FCA rules for authorized crypto businesses
- Asia-Pacific: Varying national regulations and licensing requirements
Emerging Wallet Technologies
Next-Generation Cold Storage
Innovation continues in cold storage technology:
- Biometric Authentication: Fingerprint and facial recognition integration
- Quantum-Resistant Encryption: Preparation for quantum computing threats
- Air-Gapped Smartphones: Dedicated devices that never connect to internet
- Distributed Key Storage: Splitting keys across multiple secure locations
- Smart Card Integration: Banking-grade security in credit card form factor
Advanced Hot Wallet Features
Hot wallets are becoming more sophisticated:
- AI-Powered Security: Machine learning for fraud detection
- Social Recovery: Trusted contacts can help recover lost access
- Programmable Wallets: Smart contract-based wallet logic
- Cross-Chain Bridges: Seamless asset transfers between networks
- Integrated DeFi: Native yield farming and staking features
Hybrid Solutions
The future may belong to hybrid approaches:
- Smart Cold Storage: Hardware wallets with limited connectivity
- Threshold Signatures: Combining multiple security methods
- Time-Locked Transactions: Delayed execution for security
- Conditional Access: Context-aware security policies
Recommended Wallets by Category
Best Cold Wallets
- Ledger Nano X - Premium hardware wallet with mobile support
- Trezor Model T - Open-source with touchscreen interface
- Tangem Wallet - Card-based NFC hardware wallet
Best Hot Wallets
- MetaMask - Industry standard for Ethereum and DeFi
- Trust Wallet - Multi-chain mobile wallet
- Phantom - Leading Solana ecosystem wallet
Hybrid Solutions
- MetaMask + Ledger: Best of both worlds for Ethereum users
- Keplr + Ledger: Secure Cosmos ecosystem participation
- Gnosis Safe: Multi-signature smart contract wallet
- Casa: Collaborative custody with recovery options